Method whitelisting
Motivation
Whitelisting callers introduces a level of security in cases where
- the class holding the calling method has a (too) different purpose than to be derived from the class holding the (protected) method to be called in order to inherit the same
- methods contained in different classes are to be permitted to call a specific method of another class (without inheriting the same)
- the programming language used does not support protecting methods (restricting visibility) or does not support objects at all (but just functions)
Benefits
Method whitelists provide a mean to restrict calling public methods to defined (trusted) calling methods. This affects “inner security”, which refers to an accidental misuse of a public method by a developer as well as a potentially illegal call by malicious code injected by a threat agent.
Precondition
The programming language used needs to support a mean to access the stack trace in order to evaluate a calling class and method.
Approach
- Embed the whitelist checker (method) into a base class inherited by all classes that are to use it
- The whitelist checker takes a string array or list of the names of the methods permitted to call a target method
- On being called, the whitelist checker gets the calling method or function from the stack trace and compares it to the entries white-listed
- If the calling method or function is white-listed, execution is continued, else an exception is thrown or a fatal error is raised
Example
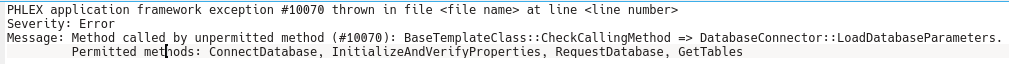
The following example (using the PHLEX application framework) demonstrates an exception on a call of a method by another (unpermitted/ unauthorized) method (the file name and line number have been anonymized). Depending on the debug level, hints regarding authorized methods may be output.
Comments are closed.